Zeta + Snowflake: Clean Room Data Onboarding Guide

Zeta ensures secure data handling through End-to-End Encryption (E2EE) when working with Snowflake. This guide walks you through how E2EE works, including internal and external staging, client-side encryption, and how to load/unload data into Snowflake using named stages securely.
End-to-End Encryption (E2EE) protects your data:
At rest (while stored)
In transit (while being transferred to and from Snowflake)
This ensures third parties, including cloud providers, cannot access your data in plaintext.
Key Components of the E2EE Workflow
Customer’s corporate network
Data file staging area:
Internal stage (provided by Snowflake)
External stage (customer-managed, e.g., S3)
Snowflake Virtual Private Cloud (VPC)
How the Data Flows
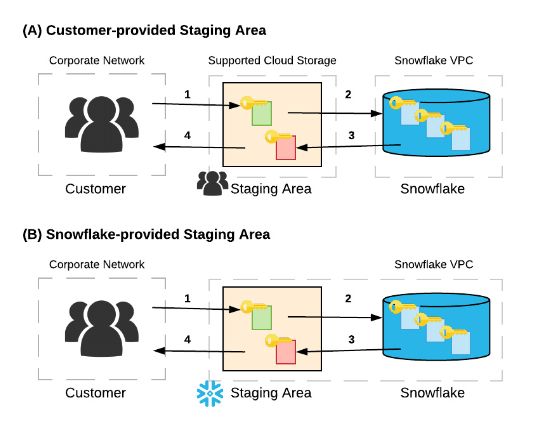
Upload to Stage
External stage (e.g., Amazon S3): You may apply client-side encryption.
Internal stage: Data is encrypted automatically before upload and again after loading.
Load into Table
Data is transformed into Snowflake’s proprietary format and encrypted both at rest and in transit using TLS.
During processing, data is decrypted and re-encrypted post-operation.
Unload Data (Optional)
Data can be unloaded to either stage type.
Client-side encryption is optional for external stages; internal stages encrypt automatically.
Download from Stage
If client-side encrypted, you decrypt locally using your master key.
Client-Side Encryption
Client-side encryption ensures your files are encrypted before they even touch the cloud.
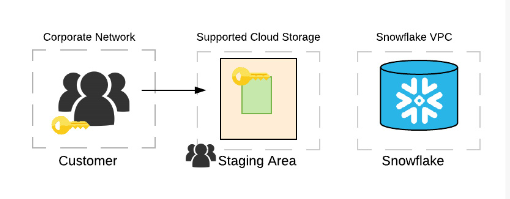
How it Works
You generate a secret master key and share it with Snowflake.
Your client generates a random encryption key to encrypt each file.
That key is then encrypted with the master key.
Both the encrypted file and key are uploaded—key stored in file metadata.
When retrieving files:
Your client decrypts the random key using your master key.
It then decrypts the file using the now-unlocked random key.
Result: No third party (including cloud providers or ISPs) can access your raw data.
Loading Encrypted Data into Snowflake
Snowflake supports secure loading via named stage objects that include your MASTER_KEY.
Step-by-Step Example
Create a Named Stage Object
Here's how to create a secure stage in S3:CODECREATE STAGE encrypted_customer_stage URL='s3://customer-bucket/data/' CREDENTIALS=(AWS_KEY_ID='ABCDE123' AWS_SECRET_KEY='XYZ987') ENCRYPTION=(MASTER_KEY='Base64EncodedKey...');Load Encrypted Data into a Table
CODECREATE TABLE users (id BIGINT, name VARCHAR(500), purchases INT); COPY INTO users FROM @encrypted_customer_stage/users;Unload Encrypted Data from Snowflake
CODECREATE TABLE most_purchases AS SELECT * FROM users ORDER BY purchases DESC LIMIT 10; COPY INTO @encrypted_customer_stage/most_purchases FROM most_purchases;
Data in customer-managed stages is encrypted using your master key and follows the defined encryption protocol of your cloud provider.
Please Note:
The
MASTER_KEYmust be AES-128 or AES-256 and Base64-encoded.Your encryption keys are transmitted securely over HTTPS and stored encrypted within Snowflake’s metadata layer.
Named stage objects allow for secure sharing within your Snowflake account without disclosing encryption keys to other users.
